
Key Takeaways
The Solana stablecoin protocol cashio suffered an “infinite mint glitch” exploit.
A hacker drained millions of dollars from the protocol and its CASH stablecoin collapsed.
Crypto Briefing has found several pieces of evidence that suggest the attacker has previously operated under the pseudonym Ariusuha to execute multiple rug pulls in the NFT space.
Share this article
The Solana stablecoin protocol cashio has suffered an exploit leading to a complete collapse of its flagship stablecoin, CASH.
cashio Hacked for Millions
cashio, a stablecoin protocol on Solana, has suffered a major exploit.
Please do not mint any CASH. There is an infinite mint glitch.
We are investigating the issue and we believe we have found the root cause. Please withdraw your funds from pools. We will publish a postmortem ASAP.
— Cashio ($CASH) 💵 (@CashioApp) March 23, 2022
The cashio team announced the incident on Twitter early Wednesday. “Please do not mint any CASH,” the team wrote. “There is an infinite glitch.” It also said it was investigating the issue and had found the likely root cause.
cashio is a Solana-based DeFi application that lets users mint CASH stablecoins. On cashio, all deposits are backed by interest-bearing liquidity provider tokens. For example, someone can provide liquidity with USDT and USDC to mint CASH. In this incident, the hacker found a vulnerability that allowed them to mint an infinite supply CASH without having the sufficient backing.
According to data from Solscan, the attacker minted two billion CASH stablecoins and then swapped them for other paired assets (mostly other stablecoins) via the decentralized exchange Saber. Per Defi Llama data, the hacker drained about $28 million worth of liquidity from the exchange. Saber posted an update announcing that it had paused its CASH liquidity pools following the incident.
As a result of the exploit, CASH, whose value is supposed to be pegged to the U.S. dollar, has completely collapsed.
While the precise extent of the damage from the attack is still officially unknown, the renowned crypto security researcher known as samczsun on Twitter said that the losses amounted to about $50 million based on their “quick skim,” of the on-chain data.
Update: Upon further investigation, Crypto Briefing has found that the person behind the cashio attack could be linked to multiple NFT-related rug pulls, including those of the ill-fated Balloonsville, Doodle Dragonz, and Fine Folk projects. The trail of evidence suggests that the person behind the cashio exploit is a 16-year-old male who used the pseudonym Ariusuha on Twitter and Discord before deleting his accounts.
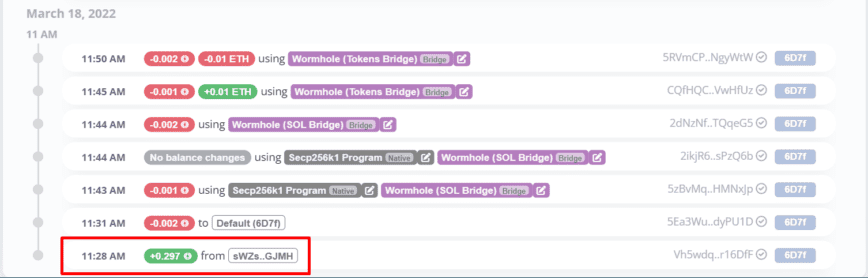
On-chain data shows that the hacker’s address, commencing 6D7f, was initially funded from another address commencing sWZs. A member of the Solana NFT community known as suavae has previously linked the sWZs address to several wallets directly connected to the exploits of the aforementioned Solana NFT projects.
Before executing multiple rug pulls in the space, Ariusuha had tried to become an NFT influencer within the Solana NFT community. A re-uploaded YouTube video, shared by suavae and allegedly originally published by Ariusuha, shows them discussing popular Solana NFT projects and revealing their age. “My name is Ariusuha. I’m 16 years-old, OK,” they say in what appears to be a male voice. “There is no place where you can just look and just get an unbiased opinion, just a real opinion from a young person, ‘cause there’s loads of young investors in NFTs but there’s no like, y’know, there’s no like big dog, y’know a young investor, who’s like telling you guys. I have money, by the way, I’m not doing this for money,” they add.
Searching the NFT marketplace OpenSea reveals that a user opened an account under the same name “Ariusuha” in February 2022. The account is connected to an Ethereum wallet commencing 0x61f and uses an avatar that bears a striking resemblance to the NFTs featured in the Solana-based project Solana Monkey Business.
A quick search using the Breadcrumbs app’s transaction mapping tool shows that Ariusuha’s 0x61f wallet has previously received funds from FTX, a centralized exchange that requires identification documents to open an account.
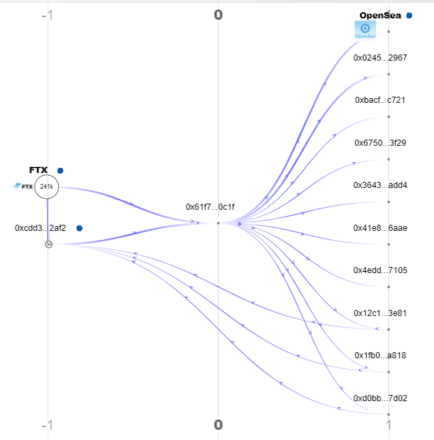
Moreover, Breadcrumbs data shows that 0x61f has also received funds from another wallet commencing 0xcDd, which has previously been funded via FTX and Binance. Given that the address is linked to interactions with multiple centralized exchanges, if the “Ariusuha” using Ethereum is the same person behind the incidents on Solana, it is likely only a matter of time before the person behind the cashio attack is uncovered.
Disclosure: At the time of writing, the author of this piece owned ETH and several other cryptocurrencies.
Share this article
The information on or accessed through this website is obtained from independent sources we believe to be accurate and reliable, but Decentral Media, Inc. makes no representation or warranty as to the timeliness, completeness, or accuracy of any information on or accessed through this website. Decentral Media, Inc. is not an investment advisor. We do not give personalized investment advice or other financial advice. The information on this website is subject to change without notice. Some or all of the information on this website may become outdated, or it may be or become incomplete or inaccurate. We may, but are not obligated to, update any outdated, incomplete, or inaccurate information.
You should never make an investment decision on an ICO, IEO, or other investment based on the information on this website, and you should never interpret or otherwise rely on any of the information on this website as investment advice. We strongly recommend that you consult a licensed investment advisor or other qualified financial professional if you are seeking investment advice on an ICO, IEO, or other investment. We do not accept compensation in any form for analyzing or reporting on any ICO, IEO, cryptocurrency, currency, tokenized sales, securities, or commodities.
See full terms and conditions.





Be the first to comment